Tuesday, November 18, 2008
-2o1o- Birthday Attack!
In probability theory, the birthday problem, or birthday paradox[1]
pertains to the probability that in a set of randomly chosen people some pair of
them will have the same birthday. In a group of 23 (or more) randomly chosen
people, there is more than 50% probability that some pair of them will both have
been born on the same day. For 57 or more people, the probability is more than
99%, reaching 100% as the number of people reaches 366.[2] The mathematics
behind this problem leads to a well-known cryptographic attack called the
birthday attack. [Wikipedia.org]
“How many birthdays does a person have in a year?”
“One”
“Then assume in a group of 23, how do we calculate the probability of a person having the same birth date as another?”
“Since the probability of one person’s birthday falls on a day is 1/365, so in a group of 23 it would be 23/365 = 6.3%”
(not taking the presence of leap years into account)
WRONG
So what’s the right way of answering this?
The simpler version of formula is
(number of people * (number of people – 1) ) / 2
(23 * 22) / 2 = 253 pairs
If you’re so inclined to find out the proper way of solving the case above, you can search for permutations and combinations on the web. Yea, and be prepared to work with big numbers.
Next, we calculate the probability of one person’s birthday DOESN’T fall on a day, and that would be
364/365 = 0.99726 (99.72%) it seems really big now but trust me, after a number of self multiplication, it shrinks really fast
we then apply the 253 as the exponent since now we are trying to get the probability of 253 pairs(group of 23).
and it would be
0.99726^253 = 0.4995 (49.95%) get what i was trying to say?
Now we’ve gotten the probability, but we are not done yet. Note that we were only focusing on the problem scenario (with the keyword DOESN’T), so in order to get the probability of a group of 23 sharing the same birth date we would do
1 – 0.4995 = 0.5005 (50.05%)
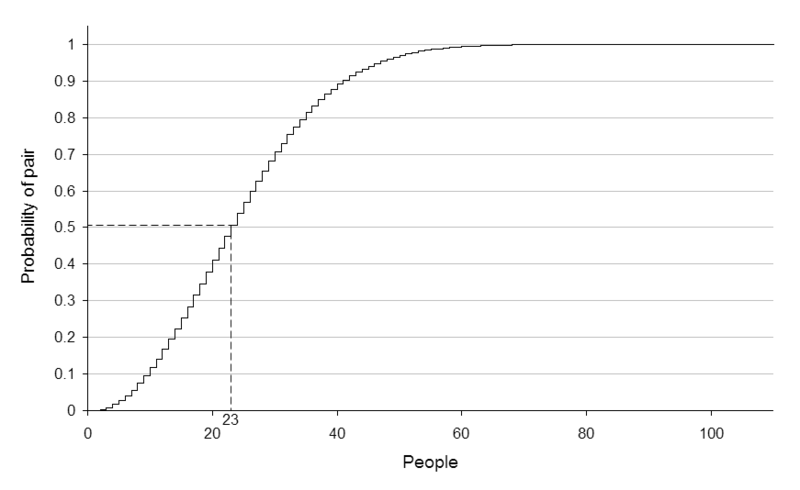
A graph showing the approximate probability of at least two people sharing a birthday amongst a certain number of people.
Now that we’ve calculated the number of pairs, the problem scenario’s probability and the actual probability. So what does it got to do with cryptography?
The Digital Signature
We are proceeding to the interesting part; let’s take the common archetypes in cryptography as an example: Alice, Bob, Mallory, Carol and Bob. Suppose that Alice wants to send an encrypted letter to Carol, and with the content that she wants to recommend Dave as the IT manager in the company, her letter would look something like
Dear Carol,
I would like to recommend Dave as the IT manager of our company because from my observation he has the potential to handle the role as an IT manager. Furthermore he is hardworking and does not late..
Then the Alice would digitally sign the letter using PGP(Pretty Good Privacy) and hand it to her secretary Mallory. However due to some personal disputes Mallory had with Dave, Mallory does not want Dave to hold the position. Hence, she would write another letter to stop Dave from getting the job and the letter would look like
Dear Carol,
I feel that Dave is not a perfect candidate for the role as the IT manager because he is often late and does not show any commitment in his work. Furthermore he does not know how to cooperate with his colleagues..
Indeed this letter would be perfect for Mallory to achieve her goal, but obviously Carol would not sign this letter and it is computationally infeasible for Mallory to obtain the private key from the digital signature. To further enhance your understanding on how the Birthday Attack takes place in this scenario, I will break down the following explanation into steps.
1. Alice is given two keys. One is called the public key and another one is called the private key.
2. The public key is given to anyone who needs it, but the private key is kept to her only.
3. Both one of the key can encrypt the data and the other key can be used to decrypt the data
4. Alice can encrypt the letter using her private key and Carol can decrypt the letter thereafter using her public key and vice versa. Mallory has the access of the encrypted letter but without the Alice's private key she can do nothing with it.
5. In order to sign a document, Alice will convert the letter into just a few lines by a process called “hashing” (ie: MD5, SHA). These few lines are called the message digest, and since it was created using one-way-hash function, it cannot be reverted back to its initial plaintext form.
6. Alice then encrypts the message digest using her private key and that would produce the digital signature.
7. Alice attaches the digital signature to the letter and passes it to her secretary Mallory, asking her to pass the encrypted letter to Carol.
8. Mallory decrypts the digital signature back to the message digest form.

We assume that the letter
Dear Carol,
I would like to recommend Dave as the IT manager of our company because from my observation he has the potential to handle the role as an IT manager. Furthermore he is hardworking and does not late..
produces the message digest
iOJfioJcioSJSfioJSVkSMflsdfkLNSgWIjfLImnvcLKFnLhfIOShfIEGNLSnbZLSHgfIHFLHGliHklvNSlgfNSLHISLIhfLnfLIjhgPQOgpGiqojOGVIAOJBKdmaKLdnVJW
and the letter
Dear Carol,
I feel that Dave is not a perfect candidate for the role as the IT manager because he is often late and does not show any commitment in his work. Furthermore he does not know how to cooperate with his colleagues..
produces the message digest
SGIOPDOPvmKFmvklNLSDKFLWGOPvjWIPGKBVmWKLVnLKTJWPFjIPtfwnMCnMFWPGUWJbpJKVCM:LKCMQJFaOIBPOKjfSFjKSfjKSLvjKLvKSjvSjdfjsf
If Mallory were to substitute the second letter with the original one and pass it to Carol, she would be able to tell that the letter has been substituted since the message digest produced by the hashing function of the second letter does not match the message digest produced by the decryption of the digital signature.
The Birthday Attack takes place
Mallory writes the letter again
Dear Carol,
I (feel think) that Dave (is not isn’t) a perfect candidate for the role as the IT manager because (he is he’s) (often always) late and (does not doesn’t) show any (commitment responsibility) in his work. (Furthermore Moreover) he (does not doesn’t) know how to (cooperate work) with his colleagues..
The ( aa bb ) denotes the alternative usage of word, which means either aa or bb can be used to produce different variation of letters while keeping the message conveyance of the letter intact. Since there are 9 combinations of alternative words, Mallory is able to generate up to 2^9 amount of similar letters using all the possible alternative pairs. Mallory would then hash all of the generated letters and given enough of combinations she would eventually be able to come up with a letter with exactly the same message digest as the original one.
For example,
Letter (257/512)
Dear Carol,
I think that Dave is not a perfect candidate for the role as the IT manager because he is always late and doesn’t show any responsibility in his work. Moreover he does not know how to work with his colleagues
Message Digest :
SfiPSJifoSJidfOSJDIONGWIOSNVISjfWPJDiMvNWkjdHSDjASHfuSHfoSHfoWSHfjSHDjhfushfOUShfJShfOSdhAODHOAhfOWSFhSJfhSdjHJSdhUShJfhSJfhJSHFj
(does not match with the original one)
Letter (412/512)
Dear Carol,
I feel that Dave isn’t a perfect candidate for the role as the IT manager because he’s often late and doesn’t show any commitment in his work. Moreover he does not know how to work with his colleagues
Message Digest :
iOJfioJcioSJSfioJSVkSMflsdfkLNSgWIjfLImnvcLKFnLhfIOShfIEGNLSnbZLSHgfIHFLHGliHklvNSlgfNSLHISLIhfLnfLIjhgPQOgpGiqojOGVIAOJBKdmaKLdnVJW
(matches the original one)
Consequently, Carol would not be able to notice that the letter has been altered since the letter generates the same message digest as the digital signature.
The Birthday Attack program
I've written a program to prove the mathematics behind the probability theory. In the program there's only one constructor, accepting two parameters.
public BirthdayAttack(int itemRange,int amount) {
I shall stick to the example given above, using the same itemRange(the days) and the amount(the number of people in a group)
public static void main(String[] args) { BirthdayAttack ba = new BirthdayAttack(365,23); ba.generate(); ba.compare(); ba.calculate(); }
The Output
Generated numbers
-----------------
39
155
191
327
352
163
121
282
8
166
210
182
331
310
29
358
352
285
71
92
66
353
28
--End of number generation--
2 352 spotted
The probability :
50.048%
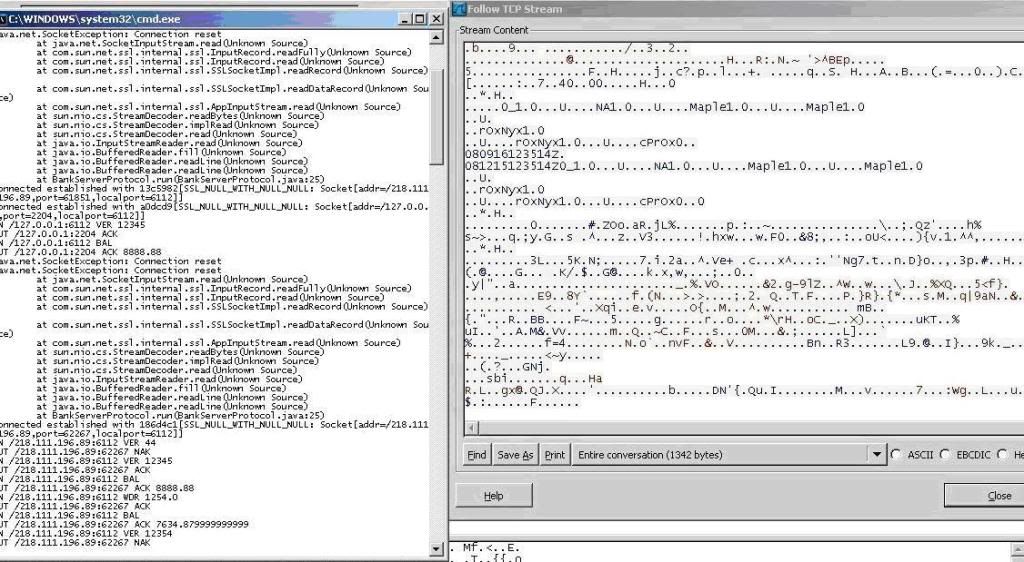
JAVA : Client-Server based ATM Simulation with SSL Encryption
Screenshots
ATMClient
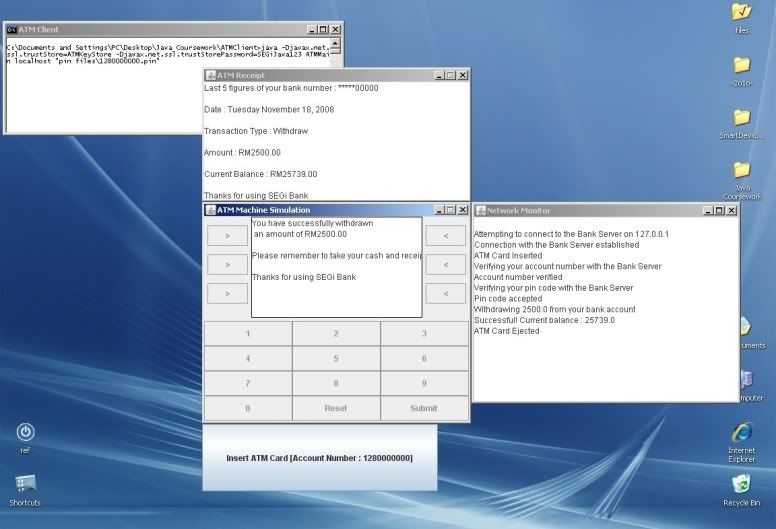
Bank Server
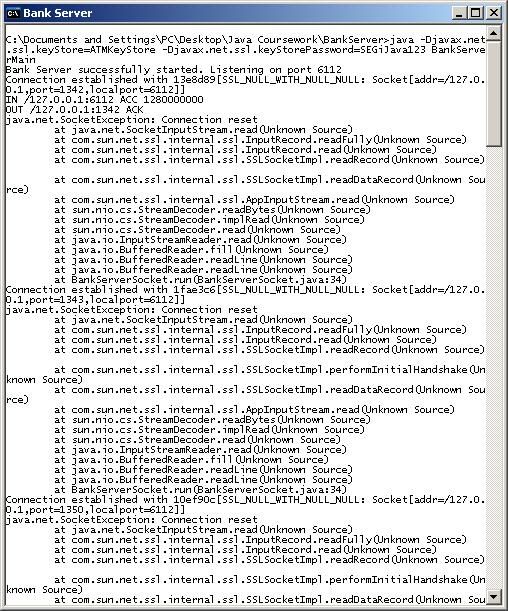
Packets before SSL encryption implementation
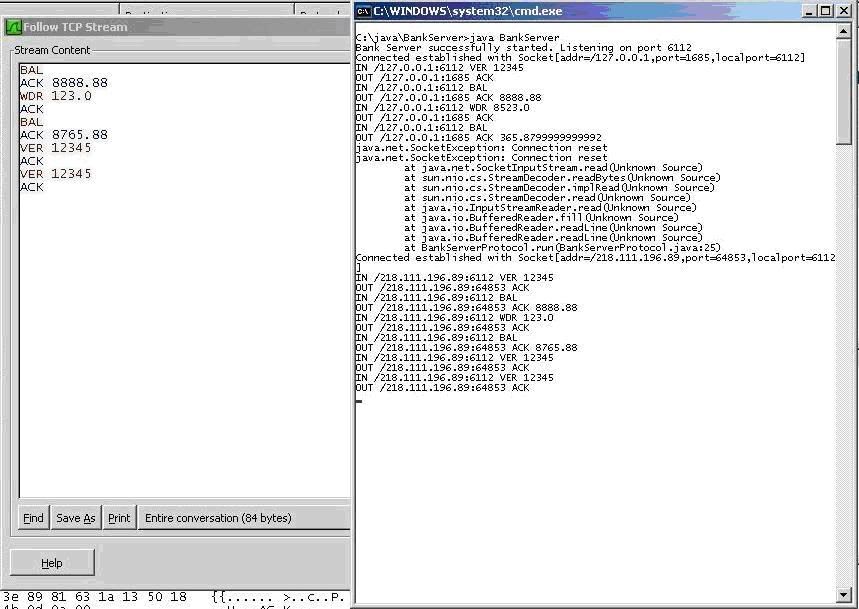
Packets after SSL encryption implementation
Introduction
Overview
The ATM simulation program is a program to simulate the real ATM machine. It provides similar functions as the real ATM machine. We will get into detail about the functions later. In brief, these are the four windows that the ATM client has: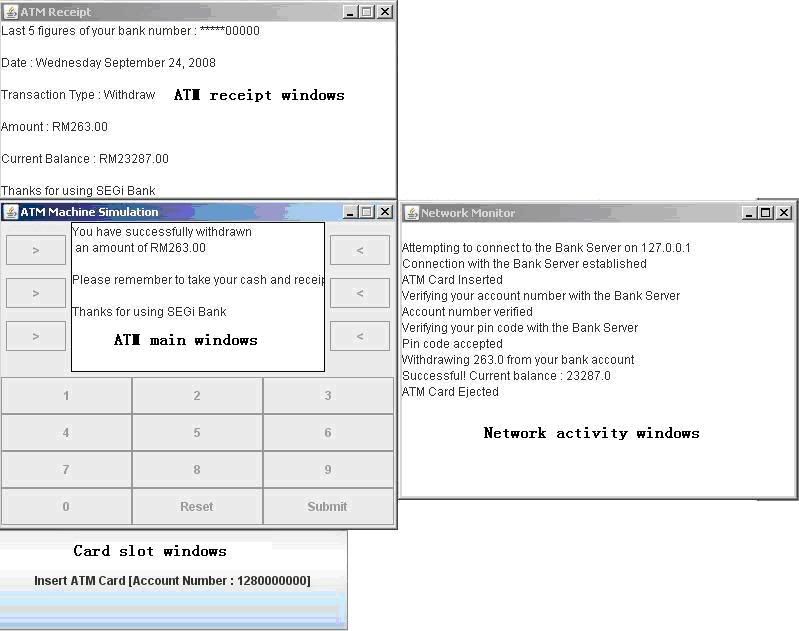
- The ATM main windows is where the user will be interacting with, to pass the request to the bank server.
- The ATM receipt windows prints the contents of a real ATM receipt.
- The ATM network activity windows which displays the user the network interaction with the server.
- The ATM card slot windows which displays the current account number in use and enables the user to insert ATM card
Programming conventions
We are pleased to say that from the knowledge that we had in our previous lectures, we were able to write the program coding that conforms most of the Java coding conventions.
The program is written based on the conventions as follows:
- Two blank lines between sections of source file, classes and interfaces
- One blank line between methods, local variables and logical sections
- Naming convention such as variable should start with a lower case letter first and constant should be in capitalized form, separated by _.
- C-style comment at the beginning of every source files
Program implementations
We also fully utilized the capability of OOP (Object Oriented Programming) concept. Since the Java does not advocate having too much of repetitive coding (similar coding perform similar action), we adopt the habit to convert the piece of coding into a method that features reusability also further reduces the complexity and the size of the whole program.
In favor of increasing the security of the program, we implemented SSL (Secure Socket Layer) into this program since in reality security is a major concern for an ATM machine. Next, we also generated approximately 500 user accounts for the user to have sufficient amount of accounts to perform simulative testing.
**To view the continuation of the documentation please download the program
Friday, October 31, 2008
-2o1o- Web Spambot v1.1.5 released!
After a few days of consideration again I've decided to release this program again, lol how indecisive I am.
Warning : Please be informed that excessive usage of this program could lead to a malady known as Denial of Service(DoS)/Distributed Denial of Service(DDoS) attack that may land you in court, and that could result in a sentence of up to a few years of imprisonment should you be found guilty. Use this program only for testing purposes or with the consent of others parties. Personally as a white hat hacker I myself do not advocate that nor am I responsible for any form of damage or harm incurred from the misuse of this program.
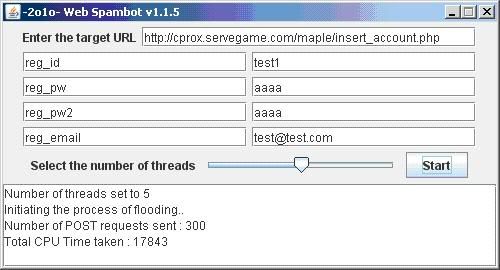
Overview of the program
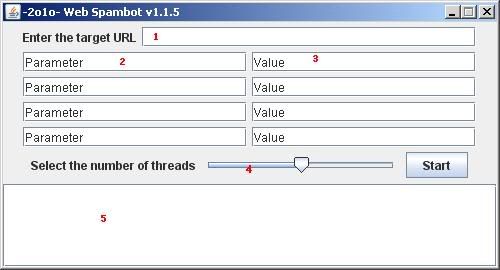
1. The target URL
2. The parameter of the POST request
3. The value of the parameter
4. Number of threads to be used
5. The status message box
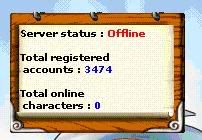
In order to further increase your understanding to operate this program, I’ll perform a live demo on one of the web hosted on my webserver. Take a look at the number of registered account, 3175; which means currently there’s an amount of 3175 accounts in my database.
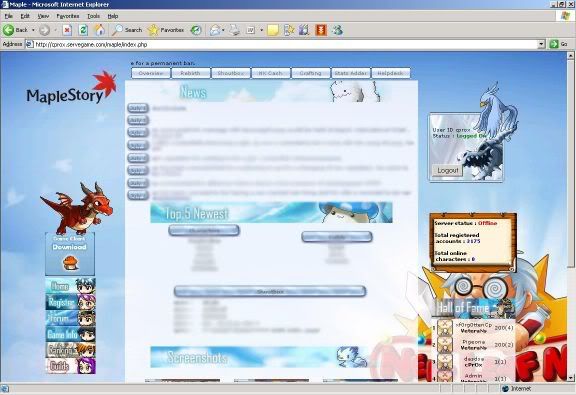
The screenshot below shows the registration form of the site. There are four mandatory fields to be filled, therefore the web spambot has to load four parameter/value fields, notwithstanding the availability of hidden fields. However this isn’t what we are going to deal with; unless you are unsure of the what value to be filled into a particular field and would like to discover the pattern of the acceptable values by playing around with the form. The main purpose of us visiting this page is to view the source code and extract the required information to perform the attack.
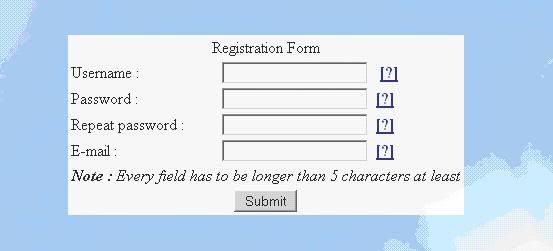
For your viewing convenience, I’ve copy pasted the source code of the registration page and marked the important elements that you should take note of. The value in red box is the page that handles the registration form’s POST requests, and it should only have one in every form. The values in blue box on the other hand are the parameters of the form, the number of parameter in a form does not have a fixed value, and the number may vary time to time. In this case we have a total of four parameters: the reg_id, the reg_pw, the reg_pw2, and the reg_email. Now we’ve gathered enough information to launch an attack.
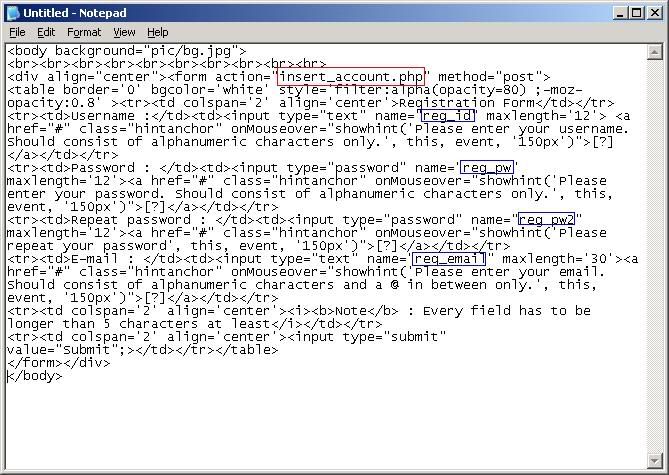
Since there are four parameters in the form and assume that I want to flood the web with 300 accounts, I would have –n 300 -p 4 as the arguments to be passed to the program.
-n denotes the number of POST requests
-p denotes the number of parameters
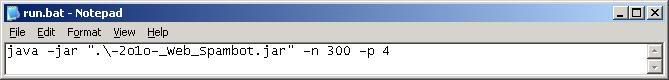
This is how the fields should look like:
click Start
and
.......
Done! 299 successive POST requests sent(299 registered accounts) in 17843 milisecs(17.8 secs).
That’s amazingly so much of deviation from the previous version of web spambot(around 74% of performance boost, not taking into account the connection latency and the nature of network performance being fluctuant when handling excessively lots of packets)
Pretty neat eh?
Warning : Even if you have the wrong parameters filled, by clicking start you and the target host would still consume considerably amount of bandwidth; the same thing happens even if the target host has your IP blocked/blacklisted, because technically the process of examining the source IP and discarding packets consumes bandwidth as well.
Number of threads versus Performance
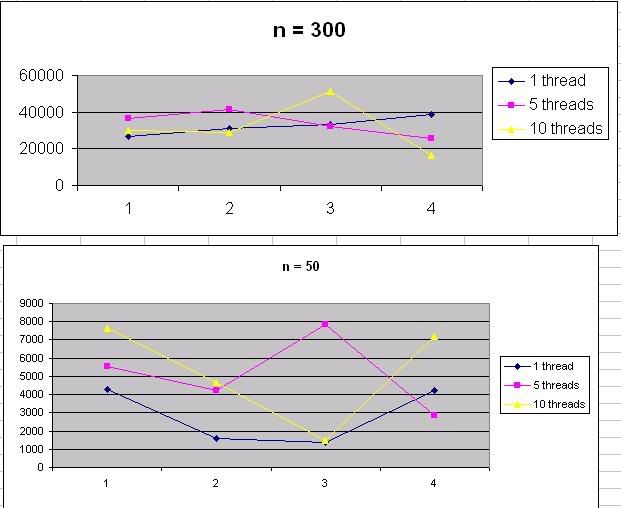
I've done a study to find out the relation between the number of threads and performance in this program using Microsoft Excel with number of POST requests, n being 50 and 300. The result of the findings turned to be somewhat out of my expectation and I don't see a clear relation of the number of threads versus performance in this program as illustrated above. For now just stick to whatever number of threads you like, I will be revising the program again after I've done with my school exams and assignments.
Addons
The class diagram
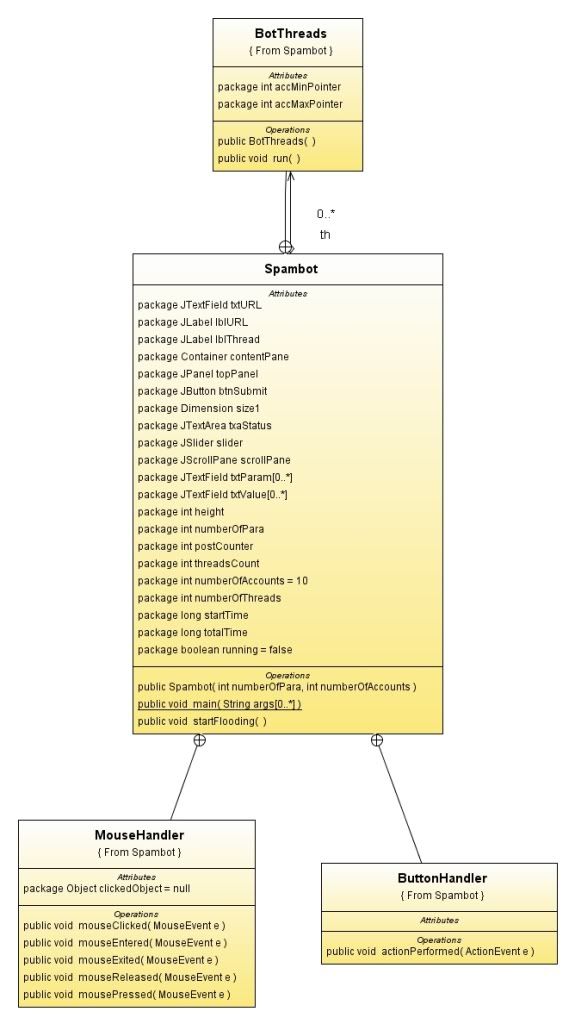
Download link : Javadocs + Source code + JAR executable + Class diagram in a bundle
Tuesday, October 28, 2008
Web spambot
Thursday, October 23, 2008
-2o1o- Cryptanalysis of Caesar Cipher
In cryptography, a Caesar cipher, also known as a Caesar's cipher, the shift cipher, Caesar's code or Caesar shift, is one of the simplest and most widely known encryption techniques. It is a type of substitution cipher in which each letter in the plaintext is replaced by a letter some fixed number of positions down the alphabet. For example, with a shift of 3, A would be replaced by D, B would become E, and so on. The method is named after Julius Caesar, who used it to communicate with his generals.
[Quoted from Wikipedia.org]
I found this cipher suit simple yet interesting, hence I brainstormed to program an utility out to perform the encryption process. You can download it here.
To encrypt a plaintext, you have to first call the insertPlaintext() method, and insert the required arguments. This method accepts only two arguments: the plaintext and the number of shifts. For instance, suppose ce is the instance of Caesar_CA() that I've created, in order to encrypt the string "testing" with the rows shift of 8, I will have to type this:
ce.insertPlaintext("testing",8);
Followed by an explicit method call of encrypt(),
ce.encrypt();
However the encrypt method does not invoke the method to display the encrypted text, you have to call the System.out.println() or similar method to display the string returned by the displayCiphertext() method. For instance,
System.out.println(ce.displayCiphertext());
Finally, the output would be
|m{|qvo
Now it comes to the interesting part; we are going to discuss about the way to decipher the ciphertext without the knowledge of the number of rows shifted through cryptanalysis. I do realise that the term cryptanalysis may be completely new to some of you, but don't worry as it doesn't require a genius to understand the underlying concept of it. Conversely, once you've gotten the hang of it, you will begin to find it interesting. In short, Cryptanalysis is the study of translating the ciphertext back into the plaintext.
For the purpose of guiding you from the scratch, I shall use the cipher suit that you are already familiar with. Take the aforementioned case as example, shifting row of the plaintext "testing" by 8 would produce the ciphertext "|m{|qvo". The decrypting process is comparatively simple, all it does is only basically reshifting the rows of the text back to its previous state. This also applies to most of the asymmetric encryptions; if you have the private key, you can decrypt the ciphertext at any point of time. Now it comes to the tricky part, also the gist of what I'm trying to deliver to you. What would happen if you do not have the private key?(in Caesar, private key is similar to the number of shifted rows) Will you still be able to obtain the initial form of the ciphertext?
The answer is obviously yes, virtually every encryption algorithm has its own way to retrieve the plaintext-form of the ciphertext's. Don't get me wrong, theoretically retrieveable does not imply that it's retrieveable in practice. Take the hash I've gotten from challenge spoofing for example: the Windows XP NTLM Security Session hash. In theory its perfectly possible to obtain the plaintext, that is, by performing an exhaustive search brute force attack. However the whole process of brute forcing would take more than millions or even billions of years, and just so you know there's no one that is silly enough to spend his/her entire life just for breaking a hash nor does he/she can live for that long. Consequently, it's practically impossible for a person to break a strong encryption but for a simple and weak encryption algorithim like Caesar, it's both theoretically and practically breakable.
In Caesar, since there are only a limited number of possible shifts.(26 for alpha combinations) One way to achieve the goal is to list out all the possible shifts in a tabular form. The program you downloaded above will demonstrate how it is done.
First, you have to call the method insertCiphertext() and pass the ciphertext into the argument. After which, you call the System.out.println() method to print the table returned by the cryptA() method.
Lastly,
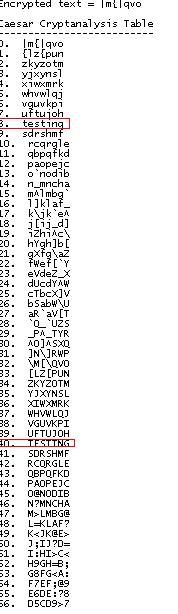
-2o1o- Does MTU affect your network latency?
-2o1o- An Example of RSA Algorithm
import java.math.BigInteger;
System.out.println("Generating Public and Private keys..");n = p * q;z = (p-1) * (q-1);
for (int i=3;i<=z;i++) {if ((z % i)!=0) e=i;for (int x=0;x<=z*3;x++) { //x has to be at least 1 time larger than z which carries the value of (p-1) * (q-1)if (((e*x) % z) == 1) {d = x;}}}
public BigInteger encrypt(int enc) {enc2 = BigInteger.valueOf(enc);n2 = BigInteger.valueOf(n);encPowE=enc2.pow(e);encPowEModN = encPowE.mod(n2);return encPowEModN; //returns the encrypted message}
public BigInteger decrypt(int decr) {decr2 = BigInteger.valueOf(decr);decrPowD = decr2.pow(d);decrPowDModN = decrPowD.mod(n2);return decrPowDModN ; //returns the decrypted message}
2o1o- Basic Mobile Application Programming Guide
- Microsoft ActiveSync
- Microsoft Visual Studio 05/08
- Windows Mobile 6 SDK
The setups for the files are pretty much straightforward so I guess it won’t be of much problem for you to get the installations done.
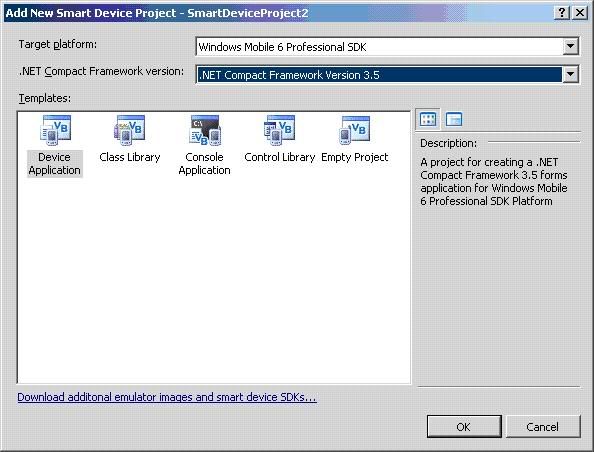
When everything is done, launch the Microsoft Visual Studio and select File -> New Project, expand Visual Basic and click Smart Device Project and then select Smart Device Project at the right portion of the windows. You may change the name if you wish to; press OK when everything is done.
Next, a dialog similar to the picture below should appear, make sure that you’ve selected the right Target platform and .Net Framework version.(It’s not a necessity to have the same settings as what shown in the picture). Press OK when you’re done.
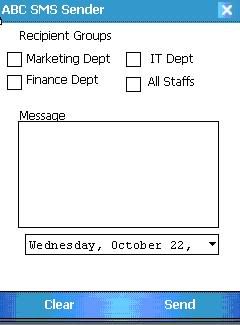
Design your form similar to the layout shown in the picture below. Again, it’s not a necessity to follow everything exactly. Just make sure that you have two textboxes for the username/password, a login button, and codes that validates the username/password combination.

Similarly, design your form in accordance with the layout shown in the picture below. The recipient groups’ checkboxes allow you to specify your target recipient. Note that within the simulative environment recipient’s number can be any combination of numbers such as 02528335 or even 1234567. For instance, suppose you have the Marketing Dept and Finance Dept checkboxes ticked, the two departments have the number of 00000 and 00001 defined respectively. Upon the transmission of the SMS, the mobile phones having the number 00000 and 00001 will receive the SMS.
The piece of code that does the SMS sending to the emulator is as follows:
where
h = The number of the recipient. For example you can do retrieve the number from a textbox like txtRecipient.text
Dim VBMobileSMS As New SmsMessage(h, g)VBMobileSMS.Send()
Before that, you have to import an external library first(place this at the topmost of the program)
Imports Microsoft.WindowsMobile.PocketOutlook
Note : If you encounter an error stating that the library could not be found, go Projects -> Add Reference and select Microsoft.WindowsMobile.PocketOutlook under .NET
Once you’ve gotten the design/coding done, hit F5 once or click the green arrow-like button, a windows should appear, asking you to select an emulator to deploy for the program. Personally I prefer running my mobile programs using Windows Mobile 6 Professional Emulator, but of course ultimately the choice is still yours. (As far as I know the difference in the type of emulator chosen does not affect your programs in any way, except the appearance of course.) Most importantly, make sure that your cell emulator is running else the emulator would not load.
Next, a mobile emulator should appear and your program will be loaded into the emulator as well. Now try to send a simple SMS, you should be able to see the message you typed in the cell emulator, similar to the picture below.
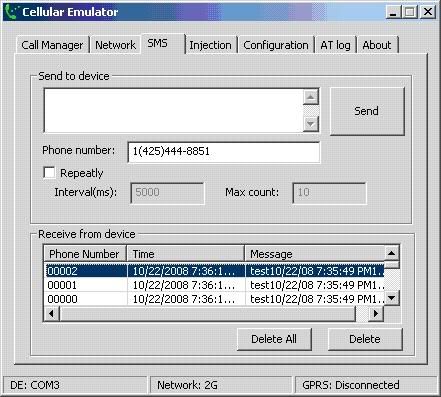
If you encounter an error stating that the COM port is unavailable or similar, check the bottom left of your cell emulator program, you should be able to see which port your cell emulator is currently using. Now go back to the deployment of the mobile emulator select File -> Configure -> Peripherals, under
You can download the program here.
CABAL : High attack or high crit damage/rate?
Red Osm single slotted weapon vs deathblow titan double slotted
Character build
rol+1 x 2 20% crit rate
lightning blade 15% crit rate
ice blade 10% crit rate
character base 5% crit rate
50% total crit rate
helm 20% crit dmg
titan(slot extended) 48% crit dmg / red osm 20% crit dmg
ice + lightning 20% crit dmg
character base 20% crit dmg
108% total crit dmg / 80% total crit dmg
eof+8 5% amp
bof+3 x2 10% amp
boots/suit/glove 21% amp
36% total amp
total atk with titan/phery 700
total atk with redosm/topaz 770
cr = crit rate
cd = crit dmg
sw.amp = sword amp
ch.amp = character amp
sk.amp = skill amp
sk.atk = skill atk
ch.atk = character atk
Formula to calc output damage
Damage rating = (cr/100)*((((sk.amp+(ch.amp/100))*ch.atk)+sk.atk)+((((sk.amp+(ch.amp/100))*ch.atk)+sk.atk)*(cd/100)))
titan phery estimated output damage= no amp involved* = (50/100)*(((1.7*700))+904)+((1.7*700)+904)*(108/100))) = 0.5*(2094+(2094*1.08)) = 2177.76
redosm topaz estimated output damage= (50/100)*(((1.7*770))+904)+((1.7*770)+904)*(80/100)))no amp involved* = 0.5*(2213+(2213*0.8)) = 1991.7
titan phery estimated output damage with 36% amp= (50/100)*(((2.06*700))+904)+((2.06*700)+904)*(108/100)))= 0.5*(2346+(2346*1.08))= 2439.84
redosm topaz estimated output damage with 36% amp= (50/100)*(((2.06*770))+904)+((2.06*770)+904)*(80/100)))= 0.5*(2490+(2490*0.8))= 2241.00
therefore we can deduce that db titan > red osm(higher damage rating)
Solution for "Cannot find eksplorasi.exe"
2. HKEY_LOCAL_MACHINE>SOFTWARE>Microsoft>Windows NT>CurrentVersion>Winlogon(Note : always consider making a backup of your regedit settings everytime before submitting any changes should any problems occur later on)
3. In the right panel of the regedit windows, you should be able to see Shell = "Explorer.exe "%Windows%\Eksplorasi.exe""
4. Delete "%Windows%\Eksplorasi.exe" located beside explorer.exe and you're done
Example : shell="Explorer.exe"

.png)


