After a few days of consideration again I've decided to release this program again, lol how indecisive I am.
Warning : Please be informed that excessive usage of this program could lead to a malady known as Denial of Service(DoS)/Distributed Denial of Service(DDoS) attack that may land you in court, and that could result in a sentence of up to a few years of imprisonment should you be found guilty. Use this program only for testing purposes or with the consent of others parties. Personally as a white hat hacker I myself do not advocate that nor am I responsible for any form of damage or harm incurred from the misuse of this program.
Overview of the program
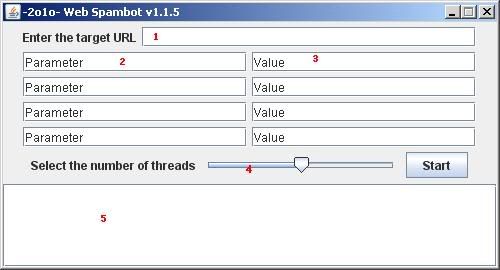
1. The target URL
2. The parameter of the POST request
3. The value of the parameter
4. Number of threads to be used
5. The status message box
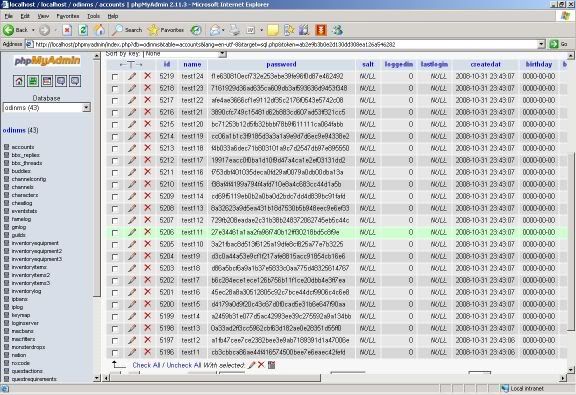
In order to further increase your understanding to operate this program, I’ll perform a live demo on one of the web hosted on my webserver. Take a look at the number of registered account, 3175; which means currently there’s an amount of 3175 accounts in my database.
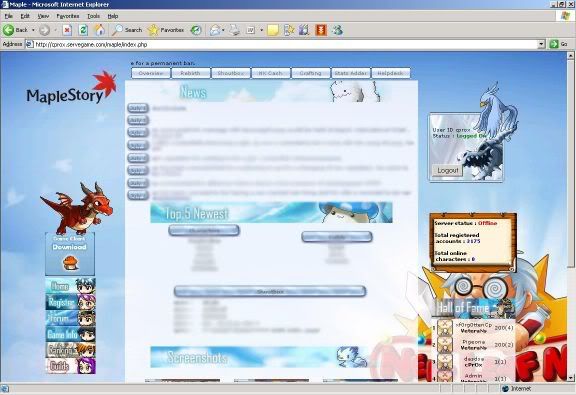
The screenshot below shows the registration form of the site. There are four mandatory fields to be filled, therefore the web spambot has to load four parameter/value fields, notwithstanding the availability of hidden fields. However this isn’t what we are going to deal with; unless you are unsure of the what value to be filled into a particular field and would like to discover the pattern of the acceptable values by playing around with the form. The main purpose of us visiting this page is to view the source code and extract the required information to perform the attack.
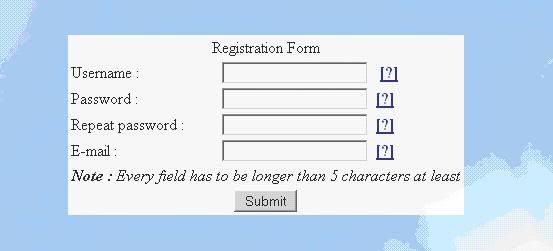
For your viewing convenience, I’ve copy pasted the source code of the registration page and marked the important elements that you should take note of. The value in red box is the page that handles the registration form’s POST requests, and it should only have one in every form. The values in blue box on the other hand are the parameters of the form, the number of parameter in a form does not have a fixed value, and the number may vary time to time. In this case we have a total of four parameters: the reg_id, the reg_pw, the reg_pw2, and the reg_email. Now we’ve gathered enough information to launch an attack.
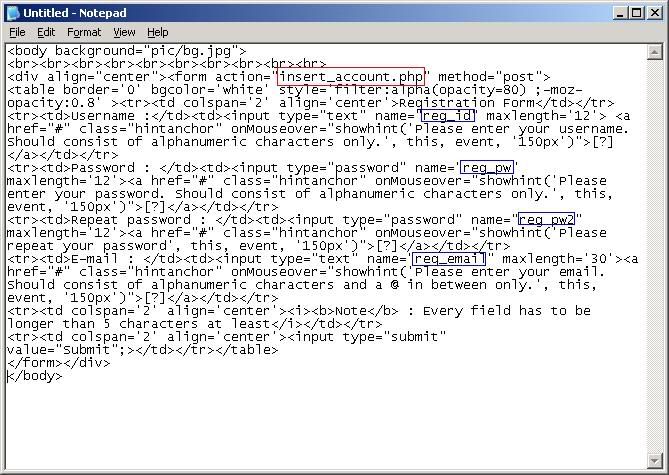
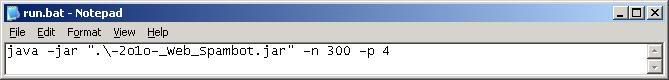
Since there are four parameters in the form and assume that I want to flood the web with 300 accounts, I would have –n 300 -p 4 as the arguments to be passed to the program.
-n denotes the number of POST requests
-p denotes the number of parameters
This is how the fields should look like:
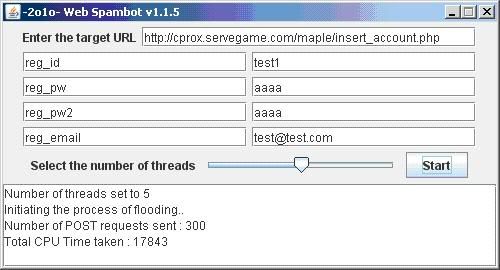
click Start
and
.......
Done! 299 successive POST requests sent(299 registered accounts) in 17843 milisecs(17.8 secs).
That’s amazingly so much of deviation from the previous version of web spambot(around 74% of performance boost, not taking into account the connection latency and the nature of network performance being fluctuant when handling excessively lots of packets)
Pretty neat eh?
Warning : Even if you have the wrong parameters filled, by clicking start you and the target host would still consume considerably amount of bandwidth; the same thing happens even if the target host has your IP blocked/blacklisted, because technically the process of examining the source IP and discarding packets consumes bandwidth as well.
Number of threads versus Performance
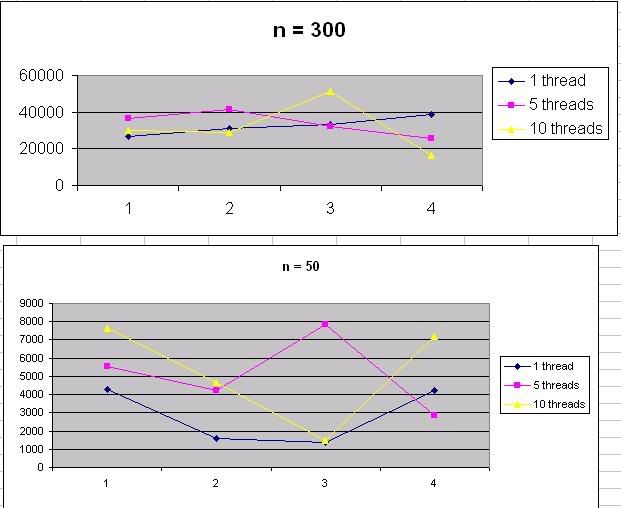
I've done a study to find out the relation between the number of threads and performance in this program using Microsoft Excel with number of POST requests, n being 50 and 300. The result of the findings turned to be somewhat out of my expectation and I don't see a clear relation of the number of threads versus performance in this program as illustrated above. For now just stick to whatever number of threads you like, I will be revising the program again after I've done with my school exams and assignments.
Addons
The class diagram
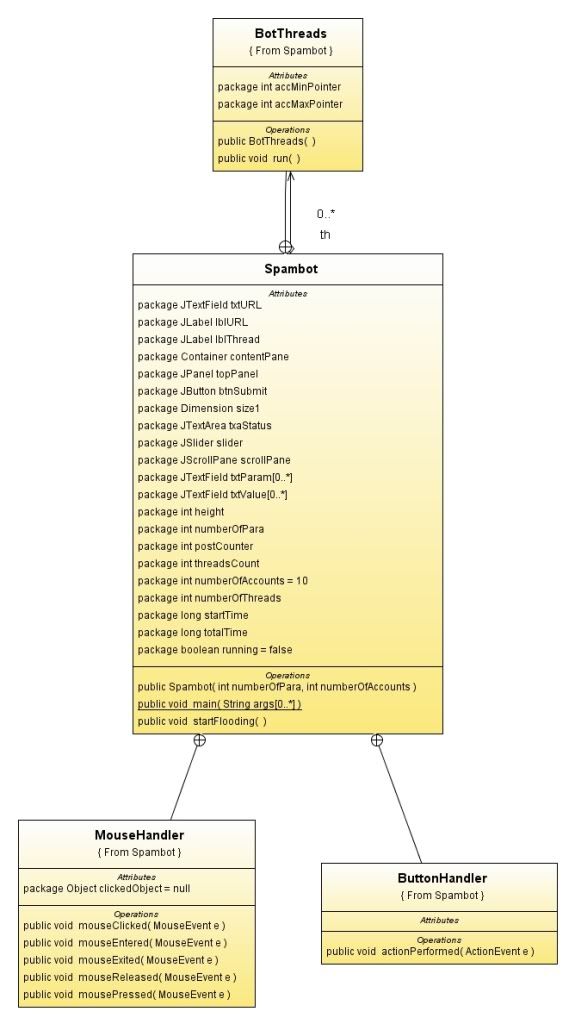
Download link : Javadocs + Source code + JAR executable + Class diagram in a bundle
.png)



No comments:
Post a Comment