When i think of writing descriptive/procedural oriented articles like what I've done in the previous article, i cringe in horror; for a simple reason that they bore me easily when it comes to writing them. On the contrary, my blood pressure tends to mount upwards as an effect of the excitement I always get by just thinking how much fun and challenge I would get in the process of writing a conceptual based article like this. Note that this article is meant for educational purposes only, I am not responsible for any loss incurred or harm caused from the practice of the skills/techniques taught.
Imagine one day when you are seated in Starbucks with a cup of your favorite Espresso and laptop by your side, listening to a business plan (which you deem not viable) of a young local entrepreneur who decided to franchise his business overseas. Boredom strikes and you decided to logon to Friendster via the wireless network to perform some social networking activities, until he finally notices your show of disinterest and leaves in utter disappointment. The next moment some anonymous guy taps your shoulder from the back and says “Hey I have your Friendster account!”
Note : You might be wondering why i chose to use a less popular site Friendster over high popularity sites like Facebook, Hotmail, and Yahoo. This is because Friendster is by far the first well established site I’ve come across, without encryption implemented in its authentication system.
The Nature of Network
Before proceeding to the interesting part, let us first fortify our knowledge on how the network transmits packets and how the router route the packets from the source to the destination. For people who do not wish to read to understand the underlying concept, you are at liberty to skip reading everything until the section “Demonstration of ARP Poisoning Attack”.
Consider the following example, user A is a home computer user with three computers connected to a router (192.168.1.1/24). One day he picked up a web designing course and decided to make a homepage of himself and host it locally. When people ask user A for the address of his newly created homepage, he would give them his IP address or domain name and people would enter the IP address/domain name in their browser, and the browser would send a SYN packet to initiate the TCP 3-way handshake process.
Everything works smooth without flaw until this point, however problem arises when the packet reaches the user A's router. His router would not be able to reach the destination because the packet contains only WAN logical IP address for itself to reach the router; it does not tell where the router should send itself to. A simple workaround for this is to send the packet to all computers connected to the router, but this apparently is not the most ideal solution, as it floods the whole network with unnecessary traffic and eventually causes traffic congestion or even Denial of Service (DoS) attack within the network.
Port Forwarding
This is where the port forwarding makes its debut in this article. Port forwarding is a NAT extension whereby the packets are directed to the intended destination by referring to the port mapping table. Of course, before everything takes place, the user has to map the port to its own logical address in order for the router to understand where to direct the packets to. Continuing from the above example, in order for the router to know how to route traffics coming to port 80 to user A's computer, it's a must for user A to map the port to his computer's IP address. After user A has done with the mapping, the router would, in essence, forward every traffic coming to port 80 to his IP address, which we assume as192.168.1.13. This also explains why a router can only have one device mapped to one port. The router however, still does not know how to reach the recipient simply by just knowing the address.
Note: A router uses NAT (Network Address Translation) to translate addresses initiated locally whereas the NAT extension “port forwarding” is used to translate address initiated outside the local network. In this article I chose to use port forwarding to explain the example because I think readers would prefer to read port forwarding over NAT.
Address Resolution Protocol
Now please allow me to introduce you the ARP (Address Resolution Protocol). ARP is a protocol used to determine the physical address (also known as MAC address) when only the logical address(IP address) is known. When a device wishes to locate another device on the same network, it would send an ARP request to every device with the message "Who has this IP Address?” and it expects the correspondent device to send back an ARP reply with the message "I have this IP address and this is my MAC address". Continuing from the above example again, the router would send every devices on the local network, says "Who has the IP Address 192.168.1.13?" and the user A's computer would send back an ARP reply "I have the IP address 192.168.1.13 and my MAC address is 00-52-FF-07-82-93". The router then sends the packet to user A’s computer and the connection ends gracefully when both parties have finished sending data and decide to terminate the session.
ARP Poisoning
Finally it comes to the wonderful part, suppose that user B, who is someone with malicious intent, happens to be living near user A and has access to his wireless network. He connects to the network, tells the router by sending an ARP reply indicating that he is 192.168.1.13(user A's IP address) and does the same to user A, indicating that he is the router (192.168.1.1). Interestingly, the router unfortunately does not know how to verify the authenticity of the ARP reply. It would only blindly thinks that user B is 192.168.1.13 and forward every packet that which is intended for 192.168.1.13 to user B. Likewise, the user A would also think that user B is the router and it would also forward every outbound packet to user B. With the possession of these packets, user B can view the contents and even launch a Man in the Middle Attack (MITM Attack) against user A.
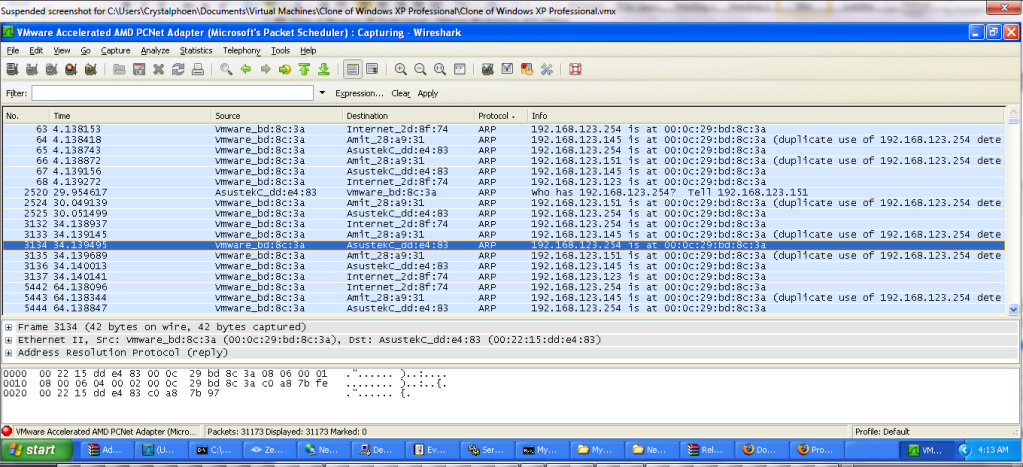
(Screenshot depicts the network activity when ARP spoofing/poisoning takes place where 192.168.123.145,192.168.123.151,192.168.123.254 are the victims and 192.168.123.123 with the MAC address 00:0c:29:bd:8c:3a is the attacker)
User B simply sends the original packets to user A and it would not raise suspicion for user A because he is essentially getting the data that he wants (unless it has been modified).
Demonstration of ARP Poisoning Attack
An ARP poisoning attack will be demonstrated below using Cain & Abel, which can be downloaded from http://www.oxid.it/cain.html
1. Activate the sniffer
2. Start ARP Poisoning
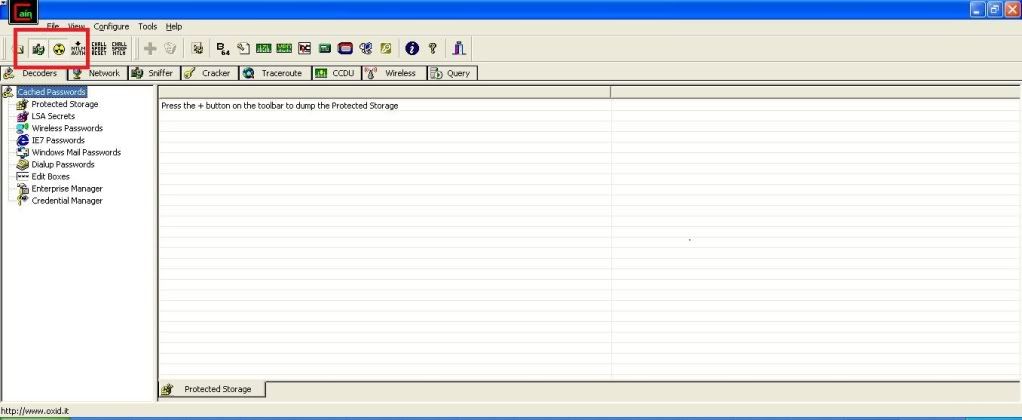
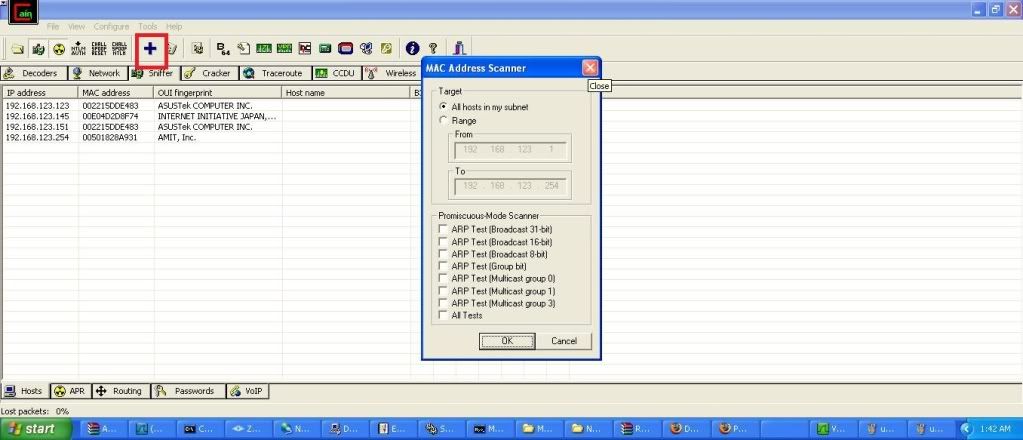
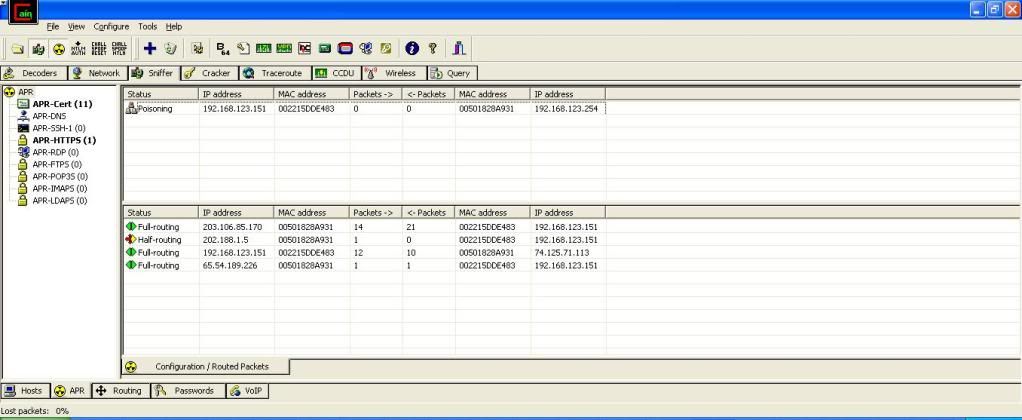
3. Click Sniffer tab and click the plus sign to scan for all MAC Addresses in the same subnet.
4. Click ARP tab and click the plus sign to add host to be ARP poisoned. Now we want to intercept the connection between the computer 192.168.123.151 and the router, which is 192.168.123.254. So we would select 192.168.123.151 and 192.168.123.254 from the list.
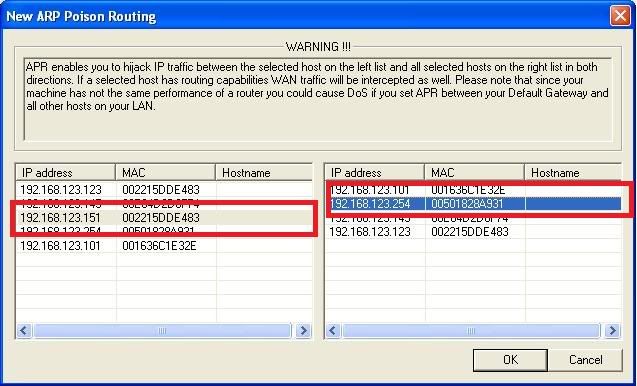
you should get something similar to the screenshot below.
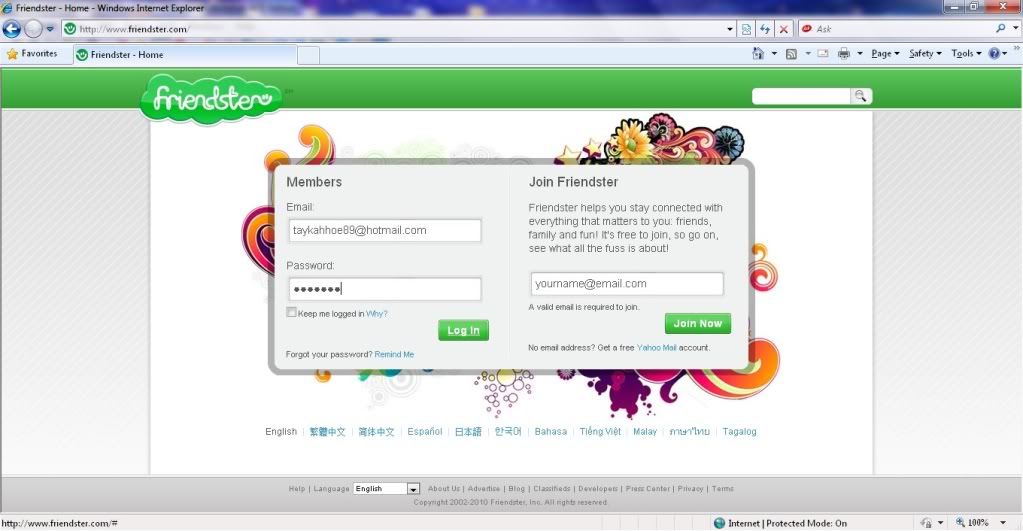
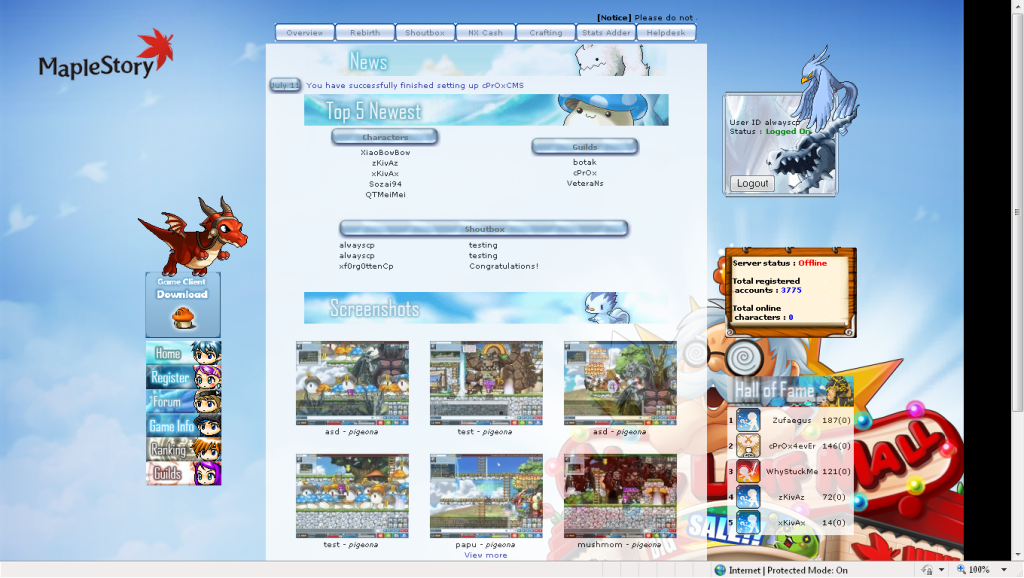
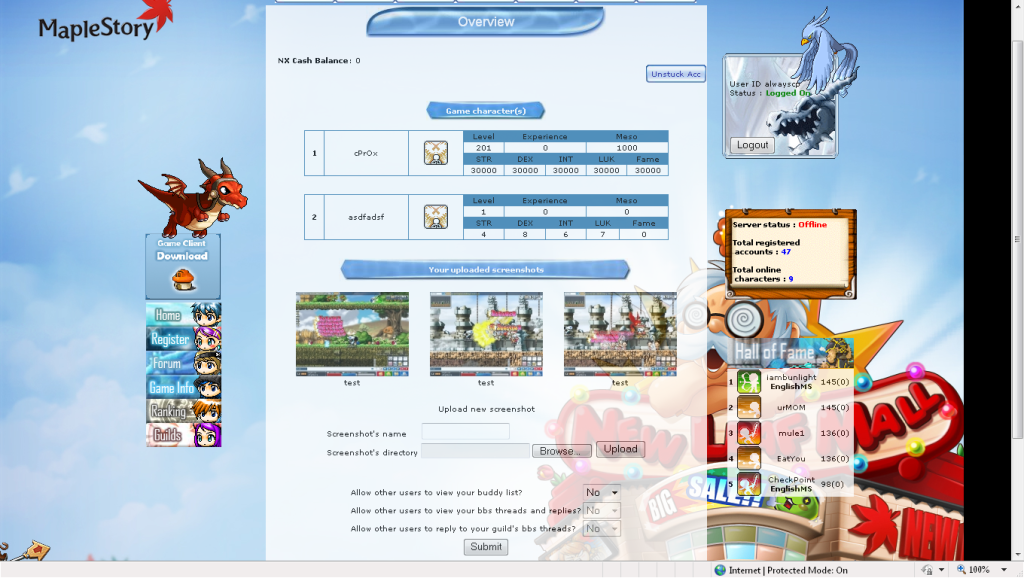
5. On another computer, I innocently enter my username and password and log into the Friendster website.
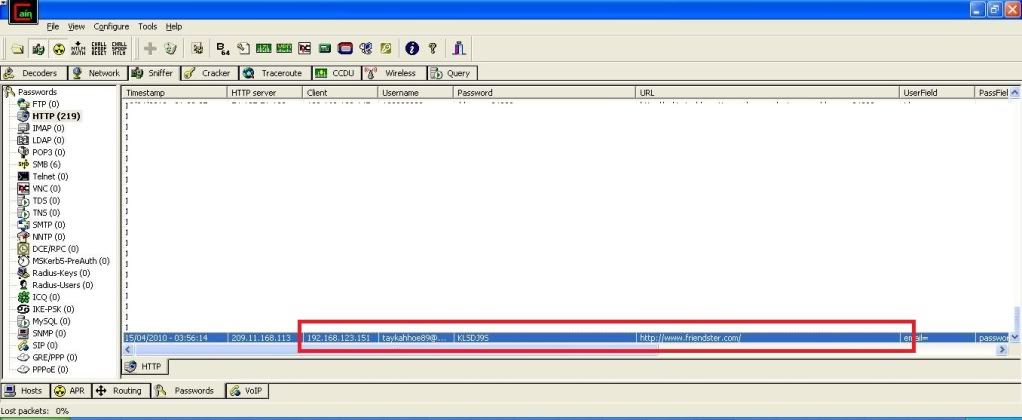
6. Click the passwords tab and select HTML, and there you see the username and password. taykahhoe89@hotmail.com and KLSDJ9S, mission accomplished.
Note: For wireless adapters, turn off the promiscuous mode if you fail to detect any MAC addresses. This should fix your problem, but you won’t be able to spoof your MAC address with promiscuous mode turned off.

.png)


